What is a zk-SNARK?

Transparency and privacy are two desirable qualities for any blockchain. However, the ability to openly track transactions while keeping personal details under wraps is not possible for all blockchains. To keep details private on public systems, you need to implement a proof system.
Proof systems use cryptographic proofs to certify that; an interaction indeed took place and its output is correct. One of the most popular proof systems are zero knowledge proofs. These proofs verify on-chain interactions without revealing any related information.
Today, there are a range of blockchain systems that implement zero knowledge proofs, and also a range of different Zero knowledge proofs themselves. One of the most important ZK-proof systems to date, has to be ZK-SNARKs.
But what is a ZK-SNARK exactly?
What is zk-SNARK?
A ZK-SNARK is a type of zero knowledge proof, a cryptographic proof which allows one party to prove it knows a certain piece of information without revealing it to others. In particular, ZK-SNARK stands for “Zero-Knowledge Succinct Non-Interactive Argument of Knowledge.”
But let's dive into what that means:
The History of ZK-SNARKs
The earliest relevant mention of ZX-SNARKs dates back to a research paper co-authored by Alessandro Chiesa, a UC Berkeley Professor. Chiesa is also the co-founder of ZCash, a privacy-centric cryptocurrency that was the first practical implementation of zk-SNARKs as a proof system to offer shielded crypto transactions.
What do zk-SNARKs do?
So you already know that Zero Knowledge proofs all aim to create a way that you can share the validity of sensitive information without revealing the information itself. But let's see the key features ZK-SNARKs use to achieve this:
ZK-SNARKs are Non-interactive
Non-interactive proof means that the prover can send the proof to the verifier without any further communication or exchange of information. This makes the proof system more efficient and practical. This property is achieved through a process known as the fiat-Shamir heuristic
ZK-SNARKs Don’t reveal sensitive information
As Zero-Knowledge proofs, ZK SNARKs ensure that no additional information other than the validity of the statement is revealed. The verifier can confirm the statement's truth but gains no extra knowledge about the specific details of the statement.
ZK-SNARKs offer Succinct arguments
Succinctness refers to the compactness of zk-SNARKs proofs and their speed of verification. These zero knowledge proofs are designed to be small in size and require minimal computational power to verify. The ”Argument of Knowledge ”is a cryptographic assertion that the prover possesses specific information or a solution. It is a stronger claim than just proof of knowledge.
Now that we have a high-level overview of what zk-SNARKs are, let’s dive into some applications & what they’re used for in the first place.
What is a zk-SNARK for?
zk-SNARKs are primarily used for 3 main applications today: scalability solutions, private transactions, and identity protection.
Scalability solutions
zk-rollups are layer-2 scaling solutions that employ zero-knowledge proofs (ZKP) to make blockchains more agile and efficient. Unlike traditional proof systems, zk-SNARKs act as proof aggregators. This means ZK-SNARKs can compile a single cryptographic proof for batched transactions.
This allows a zk-SNARK proof system to verify the correctness of all transactions quickly. The single proof concept also helps in reducing the storage and computational burden on the blockchain, improving throughput and reducing transaction fees.
Polygon Hermez and zkSync are two notable projects using zkSNARKs to solve Ethereum’s scalability concerns.
Private transactions
zk-SNARKs facilitate private transactions on blockchain by masking personal details like the sender’s and receiver’s addresses, and even the value of the transaction. Although the transaction details are hidden, the transactions are still verifiable by network validators.
Institutions can use zk-SNARKs to keep business date secure and private. From a security standpoint, private transactions also thwart blockchain front-running.
Z-Cash and Tornado Cash are projects that are enabling private transactions.
Identity protection
Every day, a person’s identity is required to access services (banking), travel (visa), and even enter a bar (age restrictions). These interactions rarely guarantee data protection and privacy.
With zk-SNARKs, a user can prove the authenticity of their identity or credentials without revealing personal information. This enhances the privacy and security of personal data while mitigating identity theft risks.
By this, trustless authentication is also made possible. This removes the need for the service providers or intermediaries to store the credentials of the users.
Zk-creds is a concept protocol that aims to use zk-SNARKs to provide flexible anonymous credentials.
How do zk-SNARKs work?
zk-SNARKs consist of three main cryptographic functions: key generation, proof generation, and verification.
zk-SNARK Cryptographic Functions and Algorithms
Key generation (setup) function:
Firstly, ZK-SNARKs rely on a key generation function as part of the initial setup phase. This function generates cryptographic keys needed for the ZK-SNARK proof system to function. Specifically, it produces a proving key (to create the proof) and a verification key (to verify the proof).
For example, C(x, w) is the logical statement that we need to verify without revealing the details. Here, ‘x’ is the public input, and ‘w’ is the private input (witness). The setup function, as a mathematical representation of this statement, takes the security parameter ‘λ’ as input. This is used to generate a proving key ‘pk’ and a verification key ‘vk’.
Setup(C,λ) → (pk,vk)
Proof generation (prove) function
The next important function: ZK-SNARKs allow provers to create a cryptographic proof — a succinct, zero-knowledge proof that the prover can send to a verifier. The prover takes the private input ‘w’ (or witness), the public key ‘x’, and the proving key pk, to produce the proof ‘prf’ that they know this information without revealing it.
Prove(w,x,pk) → prf
Verification (verify) function
The verification function in zk-SNARKs is used by the verifier to check the validity of the cryptographic proof provided by the prover. The verifier uses the proof ‘prf’, the verification key ‘vk’, and public inputs ‘x’ to determine whether or not the proof is valid. Verify(vk,prf,x) → True (if valid) or False (if invalid).
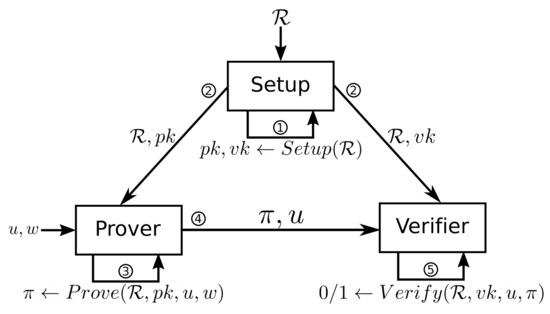
This satisfies all the three fundamental properties of a zero-knowledge proof:
- Completeness: If the initial statement C(x, w) is correct, a valid proof ‘prf’ is always generated and is accepted by the verifier.
- Soundness: If the initial statement C(x, w) is incorrect, any proof ‘prf’ generated by the prover will be deemed invalid by the verifier.
- Zero-knowledge: The verifier verifies the proof ‘prf’ without learning anything about the private input (witness) ‘w’.
Note: Both ‘prover’ and ‘verifier’ are algorithms.
The Underlying tech powering ZK-SNARKS
there are three important concepts that power zk-SNARKs. They are: elliptic curve cryptography (ECC), trusted setup, and Fiat-Shamir heuristic
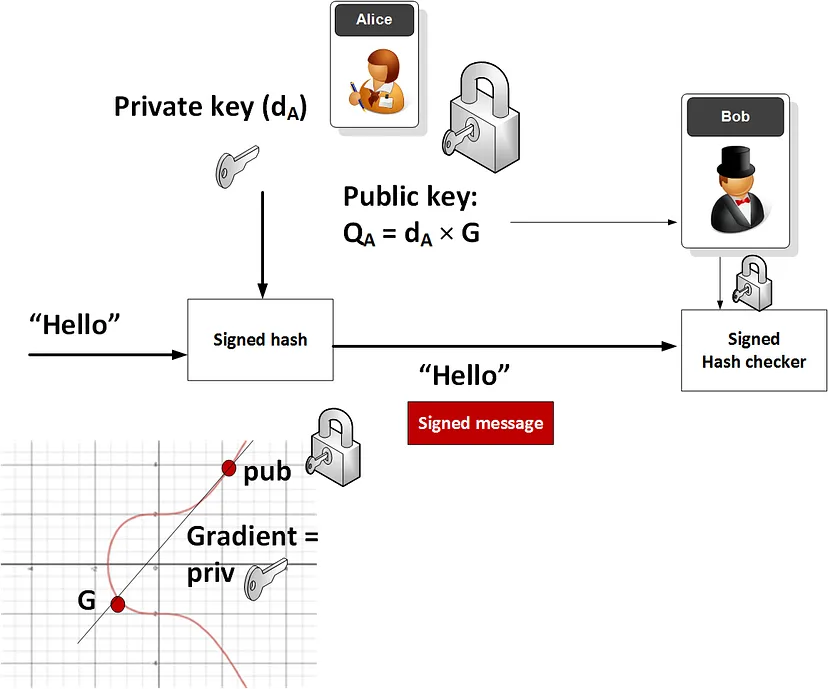
Elliptic curve cryptography (ECC)
Fundamentally, zk-SNARKs rely on elliptic curve cryptography for its security. ECC is a cryptographic approach that utilizes a twin key structure, public and private key for encryption and decryption of data.
ECC gains the upper hand over other cryptographic approaches by using algebraic structures of elliptic curves over finite fields.
A Trusted Setup
“A trusted setup ceremony is a procedure that is done once to generate a piece of data that must then be used every time some cryptographic protocol is run,” — Vitalik Buterin
Essentially, to build a zk-SNARK protocol and its public parameters, a secret is required as the basis of trust between all the participants. This secret, often called ‘toxic waste’, should be properly discarded after the initial trust setup. If not, illicit participants may exploit it to create fraudulent proofs.
A trusted setup ceremony is inherently a centralized act. The founding developers or contributors are trusted to not corrupt and game the protocol. As a deterrent, protocols now involve more participants in this setup by employing techniques like multi-party computation. This ensures that unless all participants collude, the setup remains secure. The trusted setup is a one-time requirement and is vital for zk-SNARKs' security and zero-knowledge properties.
Fiat-Shamir Heuristic
The Fiat-Shamir heuristic converts interactive proof systems into non-interactive ones by simulating the role of the verifier. Typically in an interactive proof, the verifier sends random challenges to the prover.
In the Fiat-Shamir heuristic, instead of receiving random challenges from the verifier, the prover generates the challenges themselves by using a cryptographic hash function.
To form this, we need two key elements — a functional commitment scheme and a polynomial interactive oracle.
How to get started with zk-SNARKs
You can start employing zk-SNARKs in several ways. Developers can use zk-SNARKs to add privacy to their dapps, providing a safer place for their users. Further, they can opt for blockchains like Ethereum, ZCash, and Celo that natively support zero-knowledge-proof systems.
Alternatively, developers can also deploy smart contracts with in-built zk-SNARKs to execute on-chain actions without revealing data like Tornado mixers.
If you're an EVM developer, dive into the thirdweb docs to see how you can get started with ZK-SNARKs.
zk-SNARKs: The path to blockchain privacy and scaling
Today, zk-SNARKs offer an exciting advancement for scaling blockchain networks and building a privacy-centric web3. There is a lot of effort going into making zk-SNARKs easy to use and implement, along with building an ecosystem of zero-knowledge tooling and resources.
FAQs
ZK SNARKs vs STARKs: What’s the difference?
ZK-SNARKs (Succinct Non-Interactive Arguments of Knowledge) require a trusted setup and rely on specific cryptographic assumptions such as elliptic curve pairings. ZK-STARKs (Succinct Transparent Arguments of Knowledge), on the other hand, do not require a trusted setup and are based on hash functions, making them more transparent. ZK-STARKs are also more modern and efficient than ZK-SNARKs. ZK-SNARK proofs are compact, making them highly efficient in terms of verification time and computational burden. Their faster verification times are beneficial for performance-sensitive applications.
What is the role of zk-SNARKs in zero-knowledge rollups?
zk-Rollups like Polygon Hermes use zk-SNARKs as a proof system. ZK-SNARKs bundle multiple transactions into a single proof, which is submitted to the parent blockchain i.e. Ethereum in this case. This proof attests to the validity of the batched transactions without the blockchain having to process each transaction individually. This significantly increases throughput, reduces fees, and maintains the integrity of the blockchain network.
What are zero-knowledge coins (zk-coins)?
Cryptocurrencies that use zero-knowledge proofs as their proof system are called zk-coins. They are privacy-centric in nature and generally employ zk-SNARKs to provide a shielded, censorship-free environment for transactions to take place. Monero, Tornado Cash, and ZCash are examples of zk-coins.
