Granular signing permissions for ecosystem partners

We just shipped a big upgrade to partner management for ecosystems. You can now specify what type of signatures are permitted for each partner, as well as granular controls on what exactly can be signed. As an ecosystem owner, this means you have full control of what each partner is able to do with your user's ecosystem wallets, like restricting to particular assets or actions.
In your ecosystem dashboard, you'll find a new option for "Access Control" when you create or edit an ecosystem partner. You can setup these signing restrictions in 2 ways: your own server verification, or built in rules.
Server verification
This is the most flexible and powerful option - every signature request will flow through your own server and you get to perform your own logic for allowing or disallowing a particular signature.
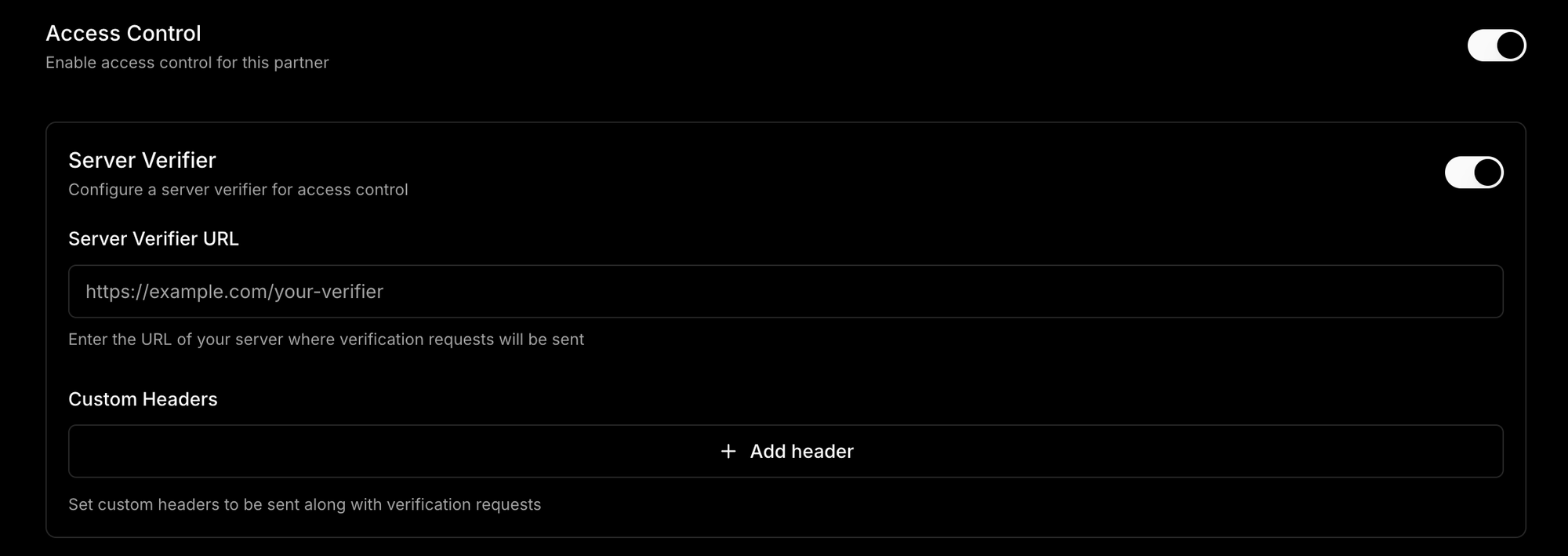
The response from your sever should just be a simple JSON body with the following format.
{
isAllowed: boolean;
reason?: string;
}Built-in rules
You can also set your rules directly in the dashboard. These include what signature types you would like to allow, and granular permissions per signature type, like the chain, contract addresses or function selectors that are allowed to be called.
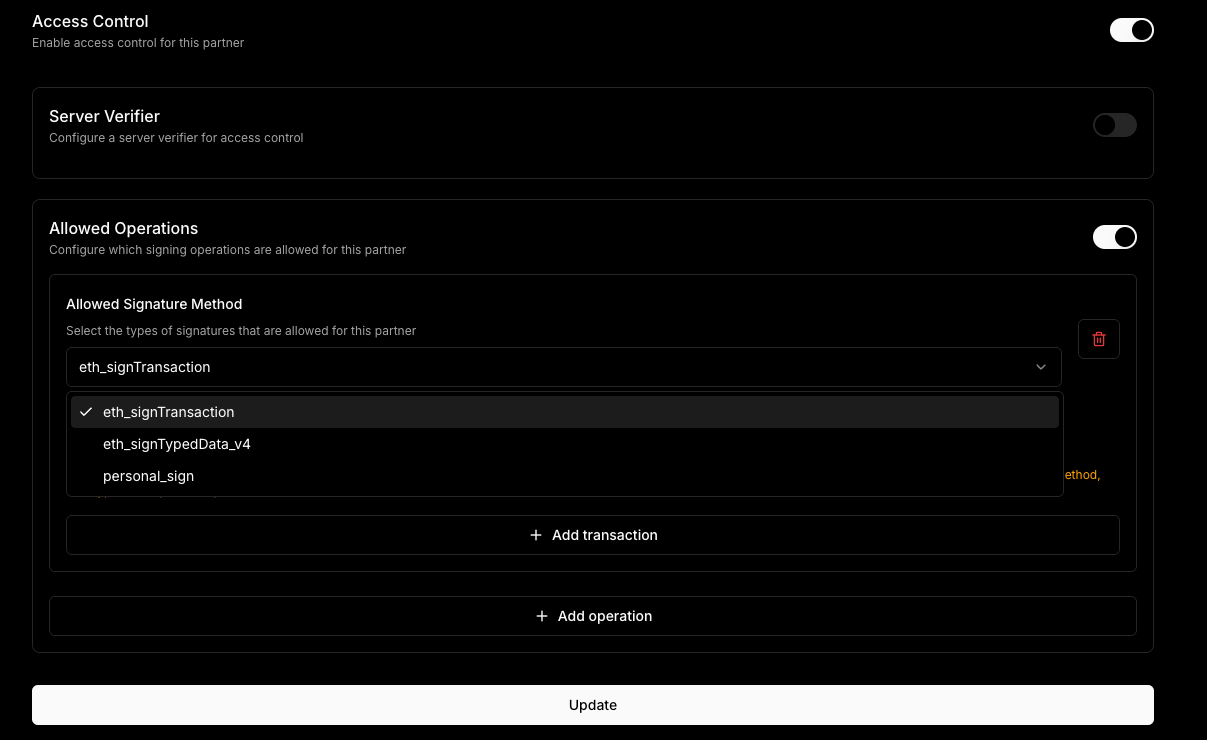
For ecosystems that use smart accounts, since those require personal_sign signatures, we've added a user operation filter that lets you control which smart account operations are allowed to be signed by the ecosystem wallets.
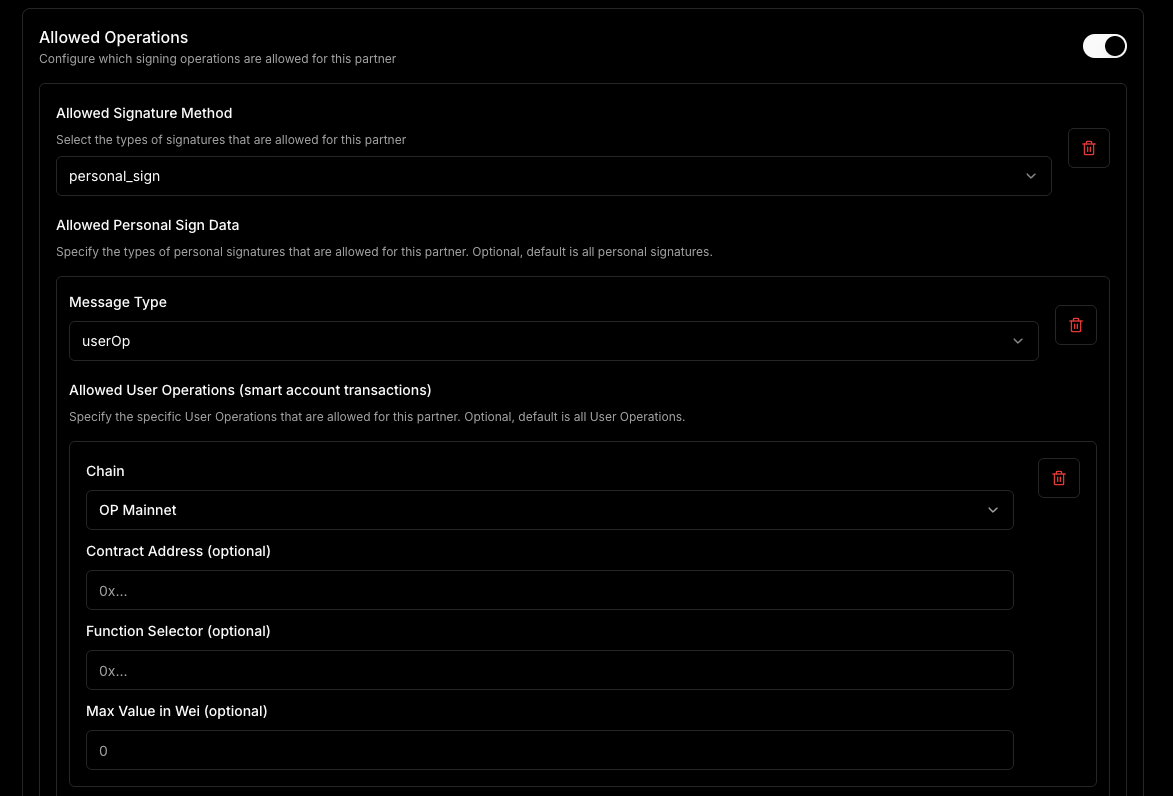
These controls are low level and powerful, letting you tightly control what can and cannot be done with wallets on a per-partner basis.
We're continuously improving this UI to make it easier for ecosystem owners to setup these rules. Your feedback is appreciated and help us make this product better for everyone!

