Smart Contract Incident Report: Auctions with a buyout price (Marketplace V3)
Summary
On September 9th, 2023, we received a security report from an independent security researcher about a critical vulnerability in the MarketplaceV3 smart contract.
The vulnerability POC (’proof of concept’) showed that an attacker can steal ERC20 / native currency escrowed in a marketplace by bidding in an auction with a bid higher than the auction’s buyout price.
We identified a total of 6 marketplaces that were compromised — having an active auction — of which 2 had at least 1 transaction in the past 10 days. A total of $0 worth of assets were at risk of being stolen, and no assets were required to be rescued.
No marketplace has suffered this exploit on mainnets. We have privately walked through mitigation steps with all admins of compromised marketplaces before disclosing this vulnerability publicly.
The vulnerability has been patched and only the fixed MarketplaceV3 contract is available to deploy across thirdweb tools, starting Monday, September 11, 2023 06:59 UTC and onward.
Bug
A marketplace contract accumulates ERC20 token and native token balance as and when the marketplace escrows bids made on an active auctions.
An attacker can drain bid funds escrowed in a marketplace by the following:
- Create an auction with a negligible buyout price.
- Bid in this auction, specifying the marketplace’s entire balance in the respective auction currency as the bid amount — effectively closing the auction.
- Collect the auction’s payout — here, the marketplace will transfer over its entire existing balance in the relevant auction currency.
The reported exploit is possible for all versions of MarketplaceV3. The reported exploit is not possible for MarketplaceV2 and prior.
The bug was introduced in the MarketplaceV3 contract in this commit where we perform an incorrect state update in the bidInAuction function.
Mitigation
Using private communication channels (discord, email and slack), we have walked through mitigation steps with all admins of compromised marketplaces.
The mitigation steps included:
- Revoking the ‘LISTER’ role from all role holders to prevent creating any new listings on the compromised marketplace.
- Setting marketplace platform fee to 100% to disincentivize any further trading activity on the compromised marketplace, and in the event of a sale, for any sale value to go to the admin of the compromised marketplace as a custodian.
- Deploying a special, new copy of the
MarketplaceV3contract that includes a migration function for either a listing creator or the admin of the marketplace to migrate over direct listings data from the compromised marketplace.
Timeline
All times are in UTC and in MM/DD/2023 date format.
- 09/09 16:37: received a security report at
security@thirdweb.comwith a POC test case and explanation showcasing the vulnerability. - 09/09 17:19: security report acknowledged via
security@thirdweb.comconfirming the reported exploit as possible forMarketplaceV3. Disabled deployments of buggyMarketplaceV3contract from all deployment surface areas on thirdweb.com. - 09/09 18:56: compiled a list of thirdweb users (known to have deployed a
MarketplaceV3contract) and associated communication channels. - 09/09 20:21: reported exploit confirmed as not possible for
MarketplaceV2and prior. - 09/09 20:55: the buggy
MarketplaceV3contract is unpublished. - 09/11 14:24: private communication containing mitigation steps sent to known admins of compromised marketplaces.
- 09/10 18:07: data collected identifying all compromised
MarketplaceV3mainnet deployments [with at least 1 active/ongoing auction and a transaction in the last 10 days]. - 09/10 23:19: acknowledgement of private communication with mitigation steps received from all admins of compromised marketplaces.
- 09/11 06:59:
MarketplaceV3republished with bug fix included; available to deploy across all deployment surface areas on thirdweb.com and the thirdweb SDK.
How it was fixed
Code fix
The fix involves reverting in the EnglishAuctionsLogic.bidInAuction function immediately, if the bid amount is greater than the auction’s buyout price.
The vulnerability has been patched in this commit.
Onchain data and understanding vulnerability impact
Since all relevant marketplace deployments are EIP-1167 minimal clones with the following bytecode structure:
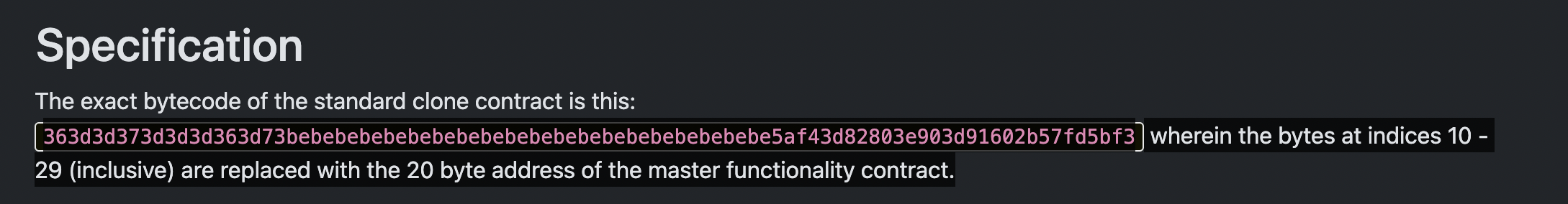
we were able to query onchain for all compromised marketplace deployments by searching for contracts with minimal clone bytecode that includes the compromised MarketplaceV3 contract’s implementation address.
- A total of $0 worth of assets were at risk of being stolen, and no assets were required to be rescued.
- We identified 6 marketplaces at risk i.e. having an active auction.
- 2 of the 6 were active contracts i.e. had at least 1 transaction in the past 10 days.
Once we identified all compromised marketplace contracts, we were able to read their state by calling the getAllValidAuctions function and determine which marketplaces had an active auction and what assets were escrowed in the marketplace.
Notifying affected users
Upon confirmation of the exploit POC, our business and customer support teams collected a list of users/teams known to have a mainnet MarketplaceV3 contract deployment. We privately communicated mitigation steps to these teams (via Discord, Slack and email).
Once we identified all compromised marketplaces via onchain data collection, we were able to identify yet un-contacted deployers and privately communicate mitigation steps to them as well.
Each contacted user/team had their own unique questions, concerns and timeline for performing mitigation. We talked and walked through mitigation with each affected team in the way that fit their needs.
Learnings
The reported critical vulnerability in MarketplaceV3 was introduced in a code change to fix a low-severity vulnerability reported in the contract’s pre-launch audit.
We have performed a thorough post-mortem with our audit partners 0xMacro about how this vulnerability slipped through the checks in our internal development pipeline and external audit process.
We’re actively revising our development process to prioritize security — exploring new Solidity tools to leverage, creating a better tests structure and writing extensive smart contract documentation — all to catch such vulnerabilities ahead of time.
If you would like to work with us in improving the security of our contracts, discuss mitigation strategies or disclose any vulnerabilities, please reach out to us at security@thirdweb.com.
